|
|

Authentication uses digital signatures to prove that a document has not been
altered. The owner of an Asymmetric Private Key creates a digest of a file
and encrypts the result. This signature can have only been created by the owner
of the private key but anyone can verify that the file digest is intact by
decrypting the signature with a public key and recomputing the original digest from the file contents.
The terminology used in digital signature and other encryption systems is summarised on this page
|
 |
|
|
|
 |
|

|
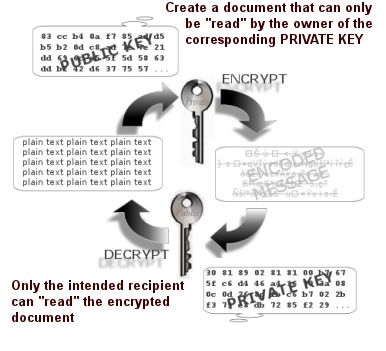
Asymmetric keys consist of a matched private key and a public
key.
Axiomatic
- If you encrypt plaintext with a private
key you can only decrypt back to the same plaintext using
the corresponding public key.
- If you encrypt with a public
key you can only decrypt with the
corresponding private key. The maths work both ways
around - but the keys don't!
The mathematics of asymmetric keys provides for an infinite number of possible key pairs. Public Key Infrastucture delegates the issue of keys to a trusted third party called a Certificate Authority (CA). The CA issues a certicate to a named user and, if the user may be trusted to have kept the private key secret, it is possible to use a encrypted digest of a file as evidence of authenticity.
f
SHA1(ALL BYTES IN FILE)→DIGEST
|
|
A digest of a
file is a short sequence produced by processing every byte in a file using a
hashing algorithm like SHA1 or MD5. It is very unlikely that two different files
will produce the same digest. A digest acts as a file or document "fingerprint"
A digital signature is a
way of proving that a data file was created or approved by the originator
and has not been changed.
f
ENCRYPT(DIGEST, PRIVATE KEY)
→
SIGNATURE
To sign a
file
- Make a digest of the file.
- Encrypt the digest with a private key.
- Record the result as a digital signature and publish with the file and the public
key
f
DECRYPT(SIGNATURE, PUBLIC KEY)
→
DIGEST
To verify a file signature is valid
- Make a digest of same
file.
- Decrypt the supplied digital signature
using the public key.
- Compare the digest with the decrypted
version.
- A certificate is used to
prove that a signature was created by a trusted originator. It
contains the originators contact details, subject and issuer information and a
copy of the public key. To prevent forgery the file containing the certificate
is itself signed by the issuer of the
certificate. This is usually a Certificate Authority that
has verified the owner of the private keys credentials.
- Verify that the signature is valid
- Locate the certificate containing the
public key.
- Check that the signature of the
certificate is valid.
- Check that the certificate has not
been revoked by the issuer.
- Check that the certificate was "in
date" when the file was signed.
- Chain through respective issuers until
a certificate is found that has been placed in a trusted certificate
store
|

